Report: Hackers Use Ethereum Smart Contracts to Hide Malicious Code
Jinse Finance reported that according to the latest report from security company ReversingLabs, hackers are adopting innovative methods by using Ethereum smart contracts to hide malicious instructions in npm packages. Two malicious packages named "colortoolsv2" and "mimelib2" appeared in July this year, and instead of hardcoding links directly in the code, they obtain the next stage of attack instructions by querying Ethereum contracts, which greatly increases the difficulty of detection and removal. The attackers also created fake cryptocurrency-themed GitHub repositories, boosting credibility by forging stars and auto-generated commit records to lure developers into adding these dependencies.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Wall Street giant Cantor Fitzgerald launches a Bitcoin and gold fund
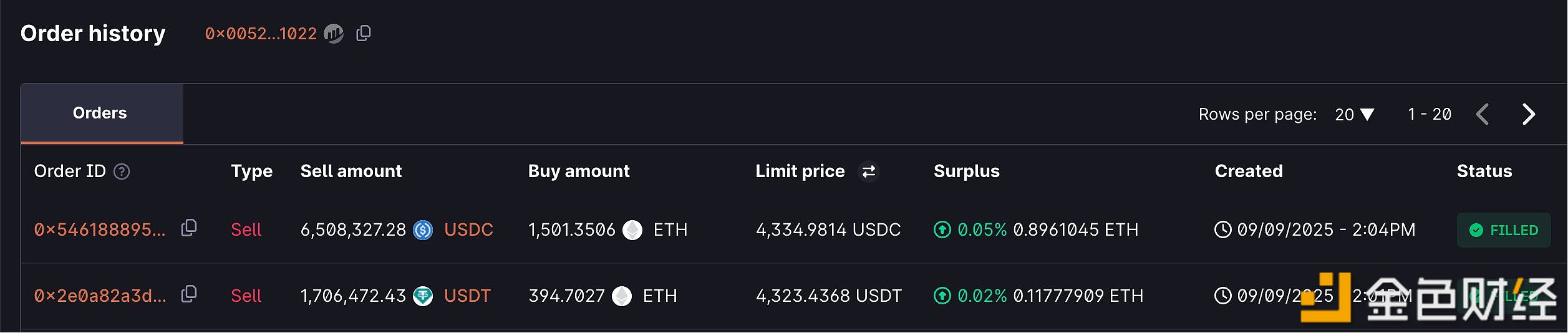
Swing whale pfm.eth spent about $8.21 million to purchase 1,896 ETH within 40 minutes
A certain whale deposited $5.17 million USDC into HyperLiquid and opened a 5x leveraged long position on HYPE.
A swing whale spent 6.508 million USDC and 1.706 million USDT to purchase 1,896 ETH.