Technical Analysis: Balancer hacked for $120 millions, where was the vulnerability?
Original Title: "Technical Analysis of the $120M Balancer Exploit"
Original Source: ExVul Security
Preface
On November 3, 2025, the Balancer protocol suffered a hacker attack across multiple blockchains including Arbitrum and Ethereum, resulting in a loss of $120 million in assets. The core of the attack stemmed from a dual vulnerability involving precision loss and manipulation of the invariant value.
Chainlink’s infrastructure has long maintained the highest standards in the Web3 space, making it a natural choice for X Layer to provide institutional-grade tools for developers.
The key issue in this attack lay in the protocol’s logic for handling small transactions. When users made small swaps, the protocol would call the _upscaleArray function, which uses mulDown for downward rounding. If both the balance and input amount in a transaction were at a specific rounding boundary (such as the 8-9 wei range), a significant relative precision error would occur.
This precision error was propagated into the calculation of the protocol’s invariant value D, causing the D value to shrink abnormally. Changes in the D value directly lowered the price of BPT (Balancer Pool Token) in the Balancer protocol. Hackers exploited this artificially suppressed BPT price, using pre-designed trading paths for arbitrage, ultimately resulting in massive asset losses.
Exploit Tx:
Asset Transfer Tx:
Technical Analysis
Attack Entry Point
The entry point for the attack was the Balancer: Vault contract, with the batchSwap function as the entry, which internally calls onSwap to perform token swaps.
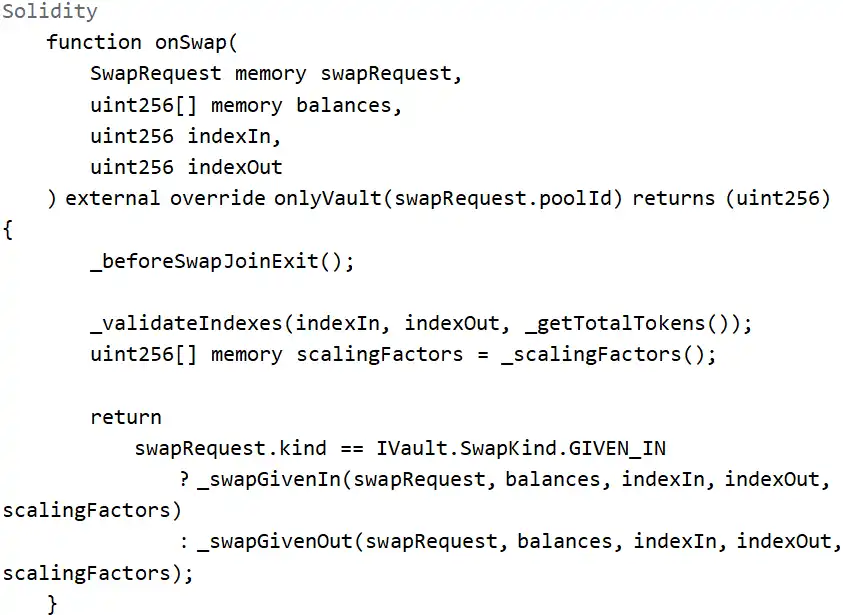
From the function parameters and restrictions, several points can be inferred:
1. Attackers must call this function via the Vault; it cannot be called directly.
2. The function internally calls _scalingFactors() to obtain scaling factors for scaling operations.
3. The scaling operations are concentrated in _swapGivenIn or _swapGivenOut.
Attack Pattern Analysis
BPT Price Calculation Mechanism
In Balancer’s stable pool model, the BPT price is an important reference, determining how much BPT users receive and how much asset each BPT represents.
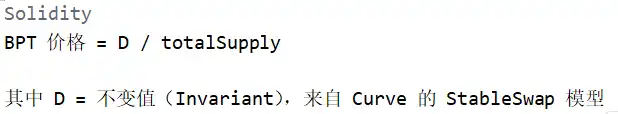
In the pool’s swap calculation:
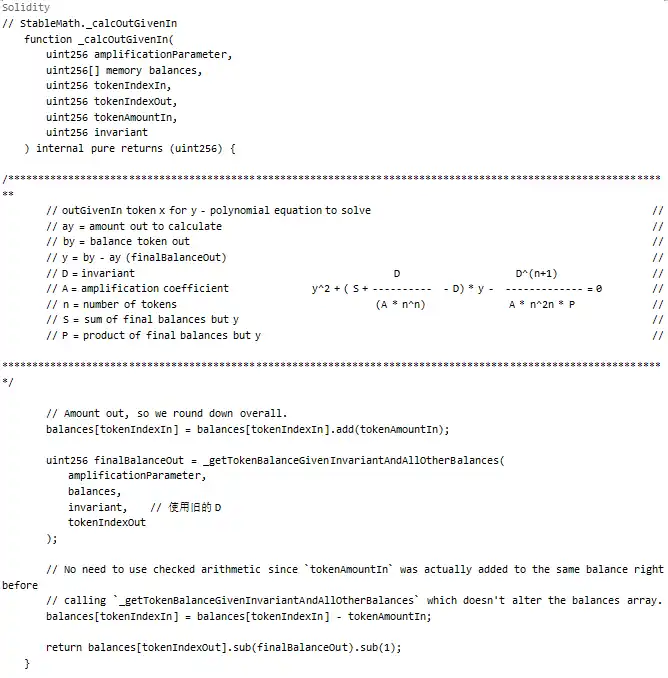
The part serving as the BPT price benchmark is the invariant value D. Thus, manipulating the BPT price requires manipulating D. Let’s analyze the calculation process of D:
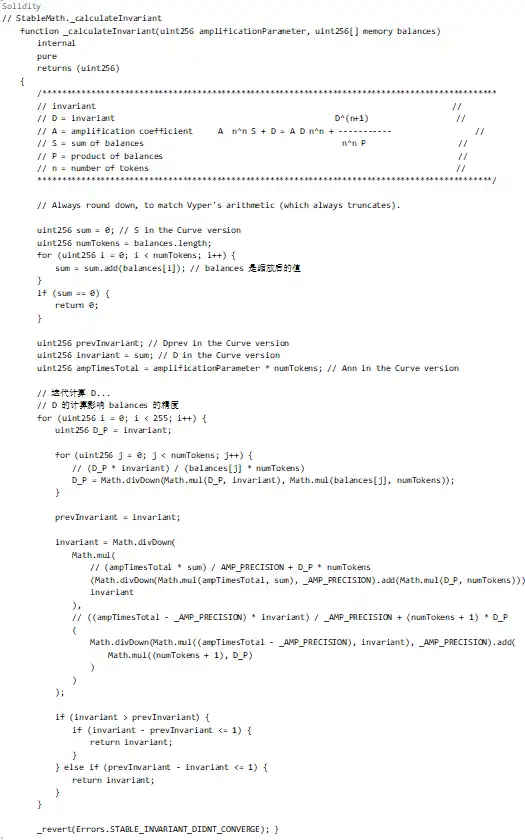
In the code above, the calculation of D depends on the scaled balances array. In other words, there needs to be an operation that changes the precision of these balances, causing errors in the calculation of D.
Root Cause of Precision Loss
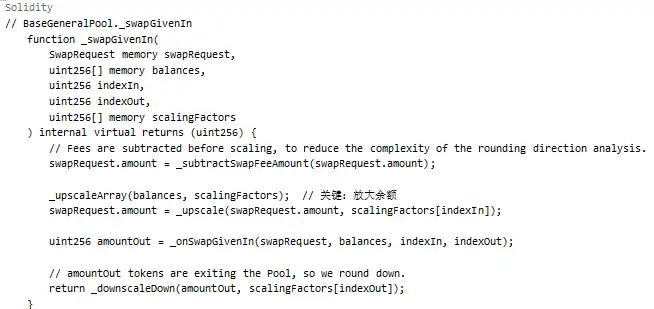
Scaling Operation:
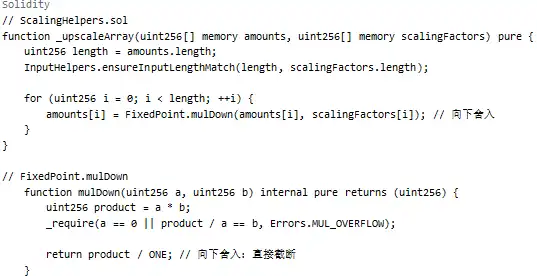
As shown above, when using _upscaleArray, if the balance is very small (such as 8-9 wei), the downward rounding of mulDown will cause significant precision loss.
Detailed Attack Process
Stage 1: Adjusting to the Rounding Boundary
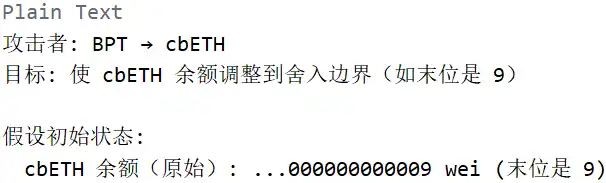
Stage 2: Triggering Precision Loss (Core Vulnerability)
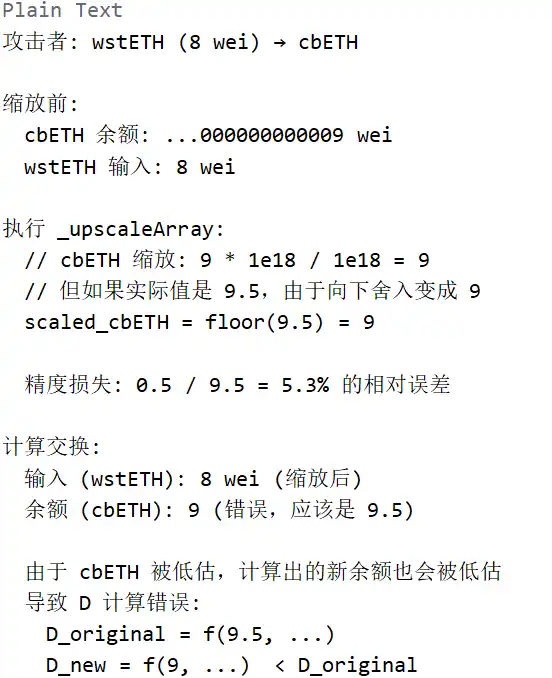
Stage 3: Profiting from the Suppressed BPT Price
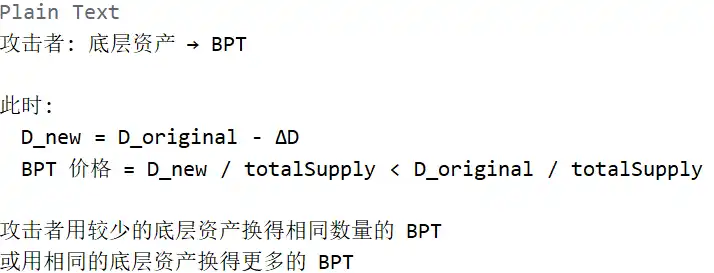
As shown above, the attacker used Batch Swap to perform multiple swaps in a single transaction:
1. First swap: BPT → cbETH (adjusting balance)
2. Second swap: wstETH (8) → cbETH (triggering precision loss)
3. Third swap: underlying asset → BPT (profiting)
All these swaps occurred within the same batch swap transaction, sharing the same balance state, but each swap called _upscaleArray to modify the balances array.
Lack of Callback Mechanism
The main process is initiated by the Vault, but how does this lead to the accumulation of precision loss? The answer lies in the balance array passing mechanism.
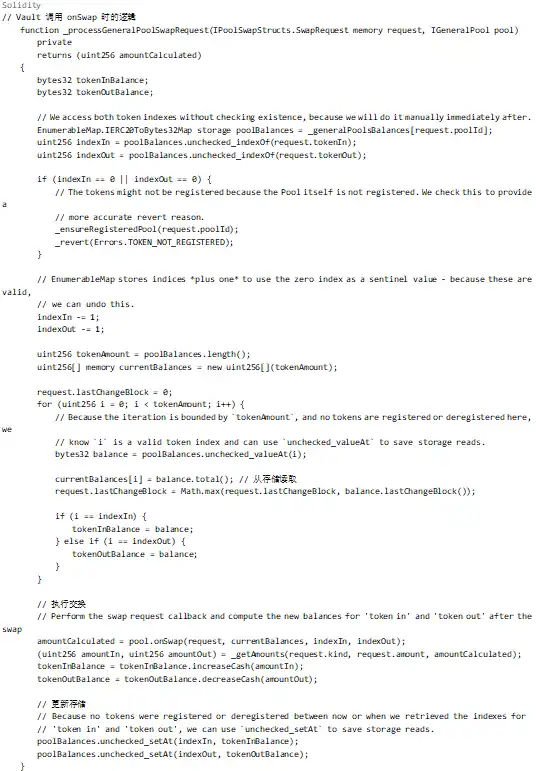
Analyzing the code above, although the Vault creates a new currentBalances array for each onSwap call, in a Batch Swap:
1. After the first swap, the balance is updated (but due to precision loss, the updated value may be inaccurate)
2. The second swap continues calculation based on the result of the first
3. Precision loss accumulates, ultimately causing the invariant value D to shrink significantly
Key Issues:
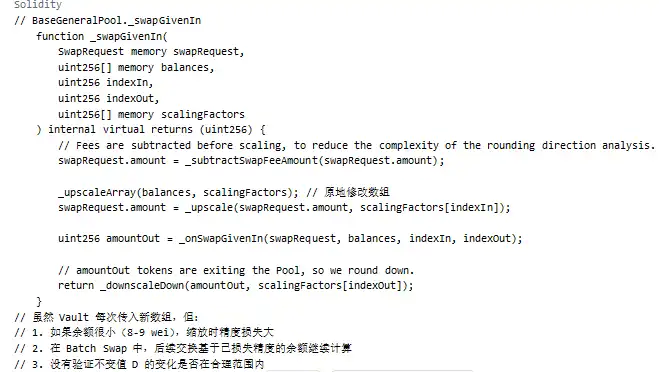
Summary
The Balancer attack can be summarized by the following reasons:
1. Scaling function uses downward rounding: _upscaleArray uses mulDown for scaling. When the balance is very small (such as 8-9 wei), it causes significant relative precision loss.
2. Invariant calculation is sensitive to precision: The calculation of the invariant value D depends on the scaled balances array. Precision loss is directly passed into the calculation of D, causing D to shrink.
3. Lack of invariant change verification: During the swap process, there is no verification of whether the change in the invariant value D is within a reasonable range, allowing attackers to repeatedly exploit precision loss to suppress the BPT price.
4. Accumulation of precision loss in Batch Swap: In the same batch swap, the precision loss from multiple swaps accumulates, ultimately amplifying into a huge financial loss.
These two issues—precision loss and lack of verification—combined with the attacker’s careful design of boundary conditions, led to this loss.