U.S. moves to seize $2.7 million from Lazarus hacks traced through Tornado Cash, other mixers
Quick Take The U.S. Justice Department has filed forfeiture actions for $2.67 million worth of cryptocurrency in the form of Tether stablecoins and Avalanche-bridged Bitcoin (BTC.b) the government says was frozen during attempts by North Korean hackers to launder the funds. The government has recovered about $1.7 million worth of Tether from the Deribit hack in Nov. 2022 and about $970,000 worth of BTC.b from the Stake.com hack in Sept. 2023.
Two recent forfeiture actions filed by the U.S. Attorney for the District of Columbia have uncovered new details about how North Korean crypto hackers launder their funds, as the U.S. government seeks to seize about $2.67 million worth of cryptocurrency stolen in two major hacks.
The forfeiture complaints, first filed on Friday, aim to recover about $1.7 worth of Tether (USDT) traced through the Tornado Cash mixer from the North Korean-linked Lazarus Group's $28 million hack of crypto options exchange Deribit in November 2022 and about 15.5 Avalanche-bridged Bitcoin (BTC.b) worth about $971,000 at current prices from the group's $41 million hack of online crypto casino Stake.com.
From Deribit to Tornado
The first of the two filings concerns the Lazarus Group's methods of laundering money from the Deribit hack through crypto mixer Tornado Cash, the service at the heart of an upcoming money laundering trial watched closely by crypto advocates. Law enforcement was able to trace some of the $28 million in funds laundered from the theft, which occurred after North Korean hackers obtained access to Deribit's hot wallet server, swapped the assets to Ethereum, and sent them through Tornado Cash to eventually wind up as Tether stablecoins on the Tron blockchain, as shown in a diagram from the filing.
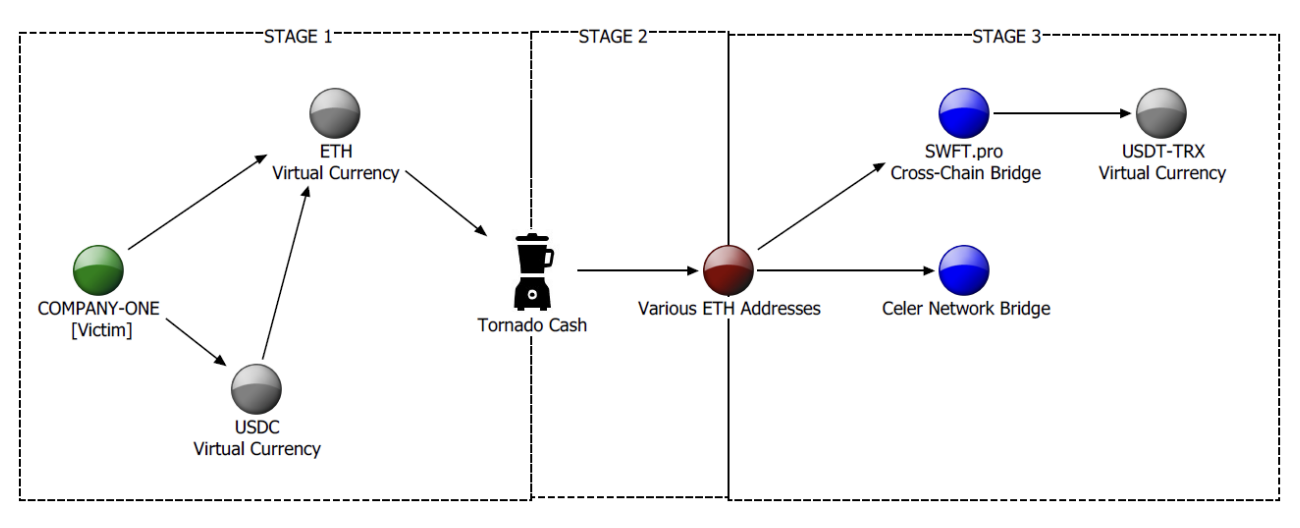
Law enforcement officials traced the funds through Tornado by noting similarities between certain Ethereum wallets. The wallets received similarly-timed transfers (within minutes of each other), utilized similar cross-chain bridges, received funding for transaction fees from the same address, and held funds which eventually wound up in the same consolidation addresses.
The hackers attempted to convert the Ethereum assets to USDT in three waves, as the first two attempts to launder the funds were halted when law enforcement froze some of the funds in question. The third attempt saw the hackers successfully launder the remainder of the funds, leaving law enforcement with about $1.7 million in USDT frozen from five relevant wallets.
From Stake.com to Sinbad, Yonmix
The second filing concerns the Lazarus Group's $41 million hack of online casino Stake.com and their attempt to launder the funds in three stages: the conversion of the funds into BTC through Avalanche's Bitcoin bridge, moving the stolen BTC through Bitcoin mixers Sinbad and Yonmix, and finally converting the Bitcoin into stablecoins such as USDT. The relevant funds were frozen during the first and third stages, likely through asset freeze requests to Avalanche Bridge.
During stage one, law enforcement froze assets from seven transactions that generally involved converting stolen assets into native tokens such as Polygon's MATIC tokens and Binance Smart Chain's BNB tokens and then bridging that value to Bitcoin through the Avalanche Bridge . However, despite the government's intervention, "the North Koreans were able to transfer the majority of the stolen funds to the BTC blockchain," the filing states.
Once on Bitcoin, the hackers used mixers Sinbad and Yonmix, which provide a service similar to that of Tornado Cash on Ethereum, to further obfuscate the movement of the stolen funds. "Law enforcement traced the flow of the stolen funds through both mixing services to the next stage of the North Korean hackers’ laundering process," the filing states, though despite identifying the consolidation wallet the officials were only able to recover an additional .099 BTC, worth about $6,270 at current prices.
Although law enforcement has improved its ability to trace and seize illicit cryptocurrency , the Lazarus Group remains active, with the group recently blamed for Indian crypto exchange WazirX's $230 million exploit among other attacks .
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
New spot margin trading pair — HOLO/USDT!
FUN drops by 32.34% within 24 hours as it faces a steep short-term downturn
- FUN plunged 32.34% in 24 hours to $0.008938, marking a 541.8% monthly loss amid prolonged bearish trends. - Technical breakdowns, elevated selling pressure, and forced liquidations highlight deteriorating market sentiment and risk-off behavior. - Analysts identify key support below $0.0080 as critical, with bearish momentum confirmed by RSI (<30) and MACD indicators. - A trend-following backtest strategy proposes short positions based on technical signals to capitalize on extended downward trajectories.
OPEN has dropped by 189.51% within 24 hours during a significant market pullback
- OPEN's price plummeted 189.51% in 24 hours to $0.8907, marking its largest intraday decline in history. - The token fell 3793.63% over 7 days, matching identical monthly and yearly declines, signaling severe bearish momentum. - Technical analysts cite broken support levels and lack of bullish catalysts as key drivers of the sustained sell-off. - Absence of stabilizing volume or reversal patterns leaves the market vulnerable to further downward pressure.
New spot margin trading pair — LINEA/USDT!
