AI threat detection crypto tools combined with strict employee vetting and dual-control wallet management can prevent insider attacks from North Korean infiltrators by flagging anomalous hiring behavior and real-time transaction anomalies before funds move off-chain.
-
Real-time AI monitors onchain and offchain signals to detect insider-driven anomalies quickly.
-
Strict background checks and role-based access limit exposure from malicious hires and impersonators.
-
Dual-control multisignature wallets and audit trails reduce the risk of large-scale fund theft; past incidents show six-figure losses from freelance infiltrations.
AI threat detection crypto: Protect firms from North Korean insider threats with real-time AI monitoring, dual-control wallets, and strict vetting. Read practical steps now.
AI threat detection and enhanced wallet management can help crypto firms detect and block insider threats from North Korean operatives, security experts say.
What is AI threat detection and how can it stop North Korean infiltrators in crypto?
AI threat detection crypto uses machine learning to correlate hiring patterns, identity anomalies and onchain transaction signals to flag suspicious behavior in real time. Implemented with strict vetting and role-based access, this approach reduces the chance that infiltrators can use employment to stage large-scale exploits.
How should crypto firms strengthen hiring and access controls?
Adopt thorough background checks, identity verification and continuous monitoring of privileged accounts. Experts including Yehor Rudytsia (Hacken) recommend strict role-based access, regular reviews of cloud permissions and enhanced logging to create auditable trails.
Security teams should treat any high-risk national-origin scenarios seriously as an operational risk. While many foreign developers are legitimate, some wages can indirectly support state cyber programs; treating this as a security vector helps mitigate systemic risk.
 Source: Changpeng Zhao
Source: Changpeng Zhao
Why are dual-control wallets and CCSS practices important?
Dual wallet control (multisignature) and CCSS-style procedures (dual control, audit trails, identity verification) limit unilateral fund movement and make exfiltration harder. These controls provide an operational barrier even if an insider has credentials.
Short, auditable workflows and mandatory multi-party approvals reduce single points of failure and improve forensic post-incident analysis.
How can real-time AI monitoring detect insider-driven exploits?
AI-driven anomaly detection links hiring data, identity signals and onchain transactions to identify patterns human teams may miss. For example, models can detect sudden changes in signing behavior, unusual developer access times, or atypical transaction patterns that precede theft.
Industry experts note that correlating offchain hiring signals with transaction anomalies is a critical capability. Deddy Lavid, CEO of Cyvers, emphasized the need for proactive AI monitoring after a recent exchange breach highlighted the dangers of delayed detection.
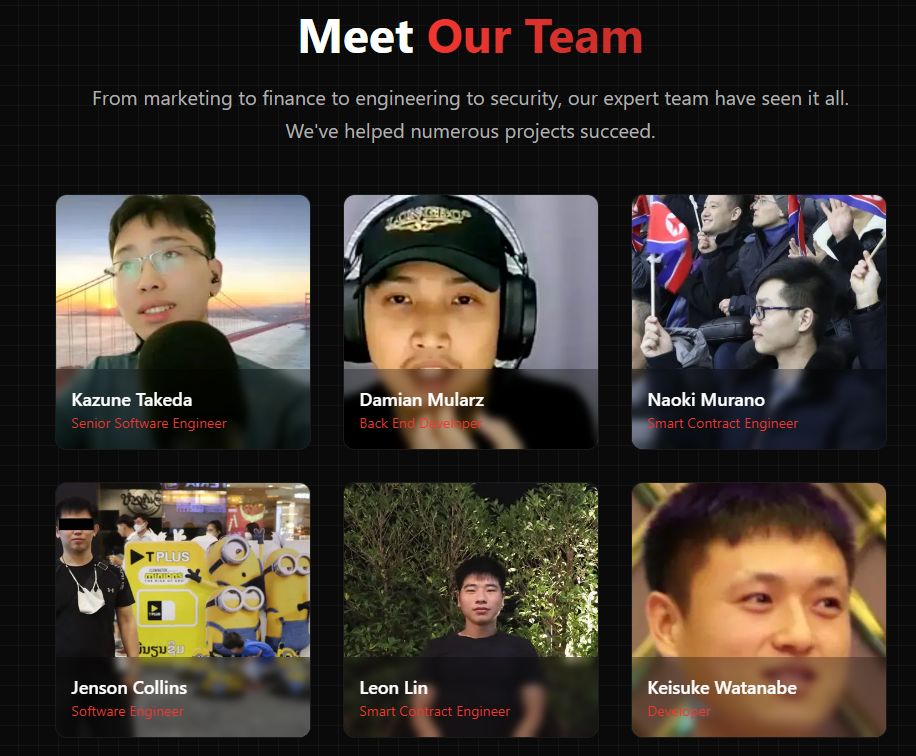 SEAL team repository of 60 North Korean IT worker impersonators. Source: lazarus.group/team
SEAL team repository of 60 North Korean IT worker impersonators. Source: lazarus.group/team
When have infiltrations led to real losses?
Recent reporting and incident data show multiple cases where infiltrators posed as freelance developers and stole funds. In one June incident four operatives stole a cumulative $900,000 from startups. Another exchange data leak exposed wallet balances and physical locations of a subset of users, highlighting the cost of poor controls.
Frequently Asked Questions
Can AI alone stop insider attacks from infiltrators posing as developers?
AI is a force multiplier but not a silver bullet. Combine AI detection with strict vetting, role-based access, dual-control wallets and regular audits to minimize risk and enable fast response to suspicious activity.
How do multisignature wallets reduce theft risk?
Multisignature wallets require multiple parties to approve transactions, preventing a single compromised or malicious user from moving large amounts unilaterally. They create checkpoints and audit trails for forensic review.
Key Takeaways
- AI monitoring matters: Link hiring and transaction data to detect anomalies early.
- Vetting and access control: Thorough background checks and role-based privileges reduce insider risk.
- Operational controls: Dual-control wallets, audit trails and logging are essential for prevention and response.
Conclusion
AI threat detection combined with robust wallet management and strict vetting forms a practical defense against North Korean infiltrators and other insider threats. Firms that front-load verification, apply CCSS-style controls, and invest in real-time monitoring will be better positioned to prevent costly breaches. Implement these measures now to strengthen operational security and protect user funds.




