OneKey responds to Milk Sad incident, confirms vulnerability does not affect the security of its software and hardware wallets
According to ChainCatcher, OneKey's Chinese Twitter stated that regarding the recent "Milk Sad incident" involving a random number vulnerability, the OneKey team clarified that this vulnerability does not affect the security of mnemonic phrases and private keys in OneKey's software or hardware wallets.
The vulnerability originates from the pseudo-random number generator in Libbitcoin Explorer (bx) version 3.x, which uses system time and the Mersenne Twister-32 algorithm, with a seed space of only 2³² bits. Attackers can deduce private keys through prediction or brute-force enumeration. The affected scope includes some old versions of Trust Wallet and all products using bx 3.x or old versions of Trust Wallet Core. OneKey stated that its hardware wallets use EAL6+ secure chips with built-in TRNG true random number generators; older devices have also passed SP800-22 and FIPS140-2 entropy tests; software wallets use system-level CSPRNG entropy sources to generate random numbers, meeting cryptographic standards. The team emphasized that users are advised to manage assets with hardware wallets and should not import mnemonic phrases generated by software wallets into hardware wallets to ensure the highest level of security.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
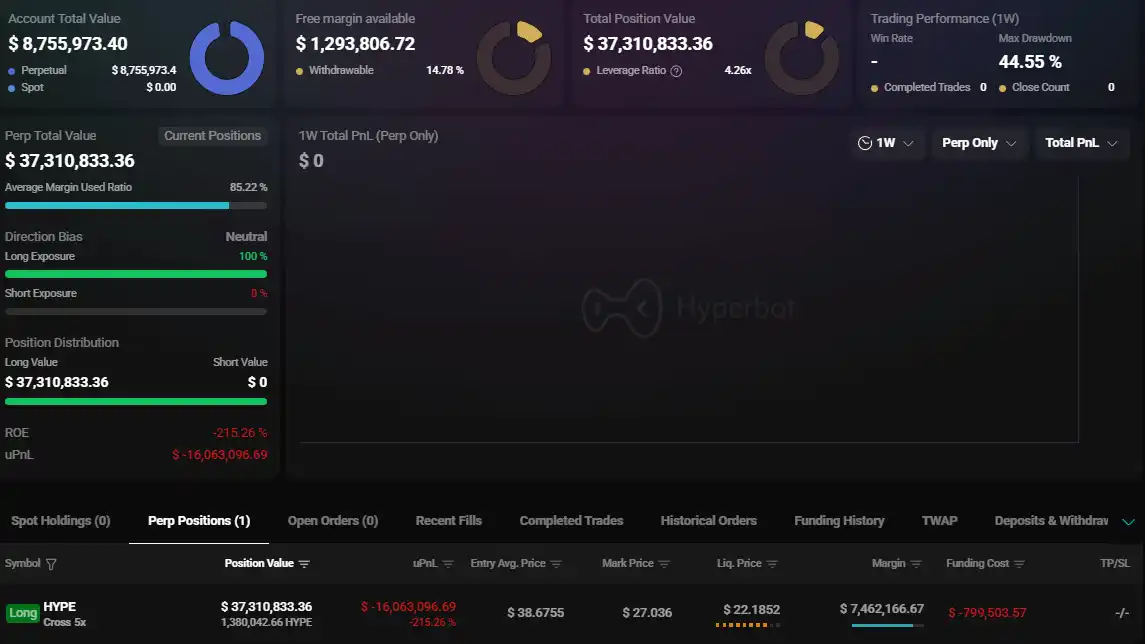
"HYPE Listing Insider Whale" suffers a floating loss of $16 million on 5x HYPE long positions
Disney to make $1 billion equity investment in OpenAI
ETH swing whale buys low and sells high, withdrew 2,779.8 ETH again 4 hours ago
